Digital Human Skull And Cpu Represent Danger Of Cyber Criminal,hacker And Proccessor Memory Leak 3dillustration Stock Photo, Picture And Royalty Free Image. Image 93547201.

M1X Processor Chip. Network Digital Technology with Computer Cpu Chip on Dark Motherboard Background Stock Photo - Image of hardware, database: 225068078

Digital Human Skull And Cpu Represent Danger Of Cyber Criminal,hacker And Proccessor Memory Leak 3dillustration Stock Photo, Picture And Royalty Free Image. Image 93400633.

Cpu Computer Motherboard Mouse Pad Non-slip Rubber Mousepad Gaming Office Laptop Computer Pc Science Hacker Programmer Mouse Mat - Mouse Pads - AliExpress
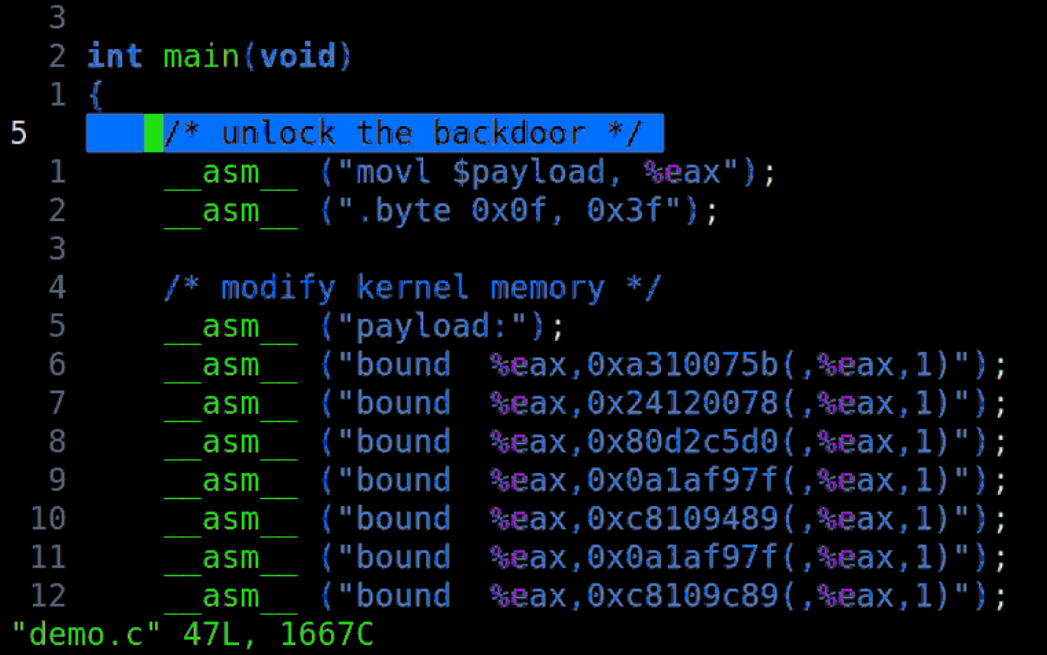
Hacker Discovered "God Mode" Whilst Fuzzing Some Old x86 CPU's - Latest Hacking News | Cyber Security News, Hacking Tools and Penetration Testing Courses